Solana development moves fast. Contracts go from local testing to mainnet in days. But speed creates risk: missing a signer check or overlooking an untested edge case can cost millions.
Today, we’re launching the first VS Code extension explicitly built for Solana developers. It brings two essential security layers directly into your editor: real-time static analysis and fuzz coverage visualization. Get instant feedback as you code, without separate tools or CI/CD delays.

What it is
The Solana VS Code extension adds security-focused development tools to your existing workflow. It runs two main features:
Real-time security analysis catches common Solana-specific vulnerabilities as you type. Nine detectors built from findings in actual production audits flag issues like missing signer checks, unsafe math operations, and improper account initialization before you even compile.
Fuzz coverage visualization shows which code paths your Trident tests actually exercise. Green highlights mark covered lines. Red highlights show untested paths. Execution counts reveal how thoroughly each line is tested.
Both features integrate directly into VS Code with zero configuration. Open your Solana project, and the extension works immediately.
Real-time security analysis
The Rust extension can catch syntax errors. It can’t catch Solana-specific security issues.
Consider this code:
#[derive(Accounts)]
pub struct UpdateConfig<'info> {
#[account(mut)]
pub authority: AccountInfo<'info>,
#[account(mut)]
pub config: Account<'info, Config>,
}
It compiles. It runs. But there’s a critical vulnerability: the authority account lacks signer verification. Anyone can call this instruction and modify the config.
The Solana extension flags it immediately with a red squiggle and a precise diagnostic: “Missing signer check on authority account.”
The nine detectors
Each detector targets vulnerabilities found in real Solana protocol audits:
- Missing signer verification
Catches accounts that need signer checks but don’t have them. Without verification, privileged functions become public.
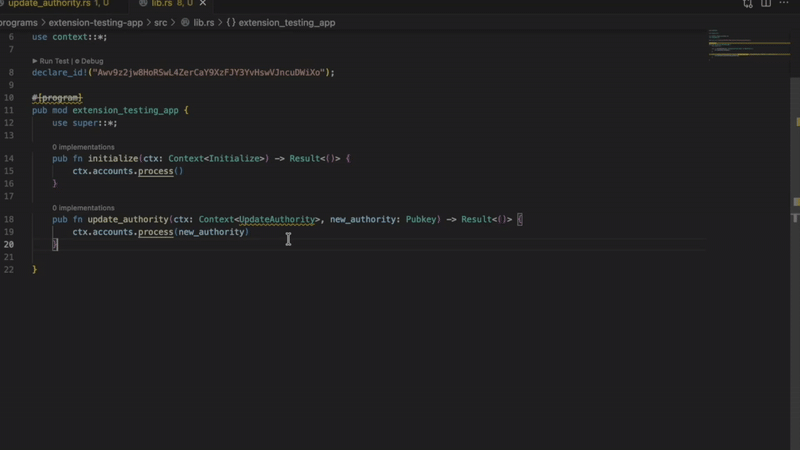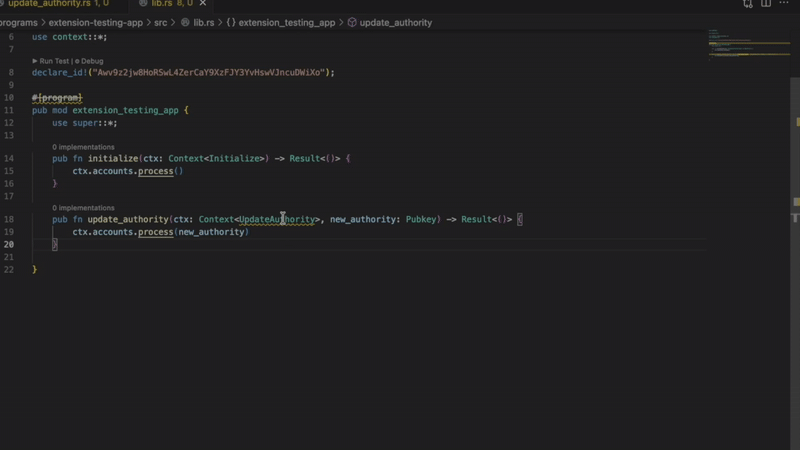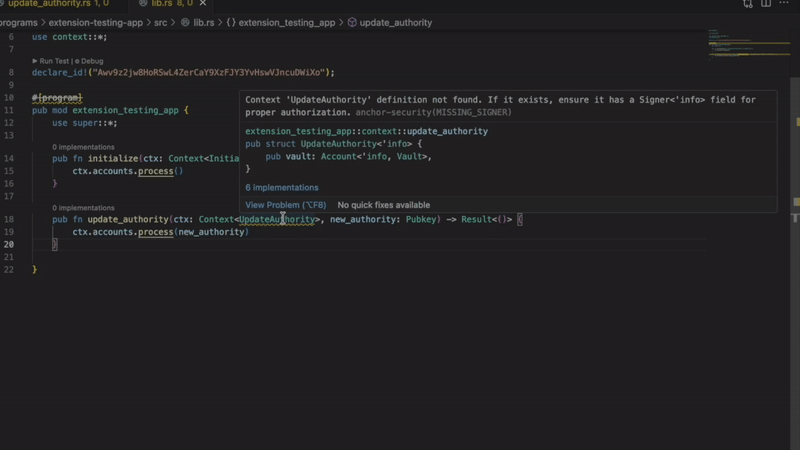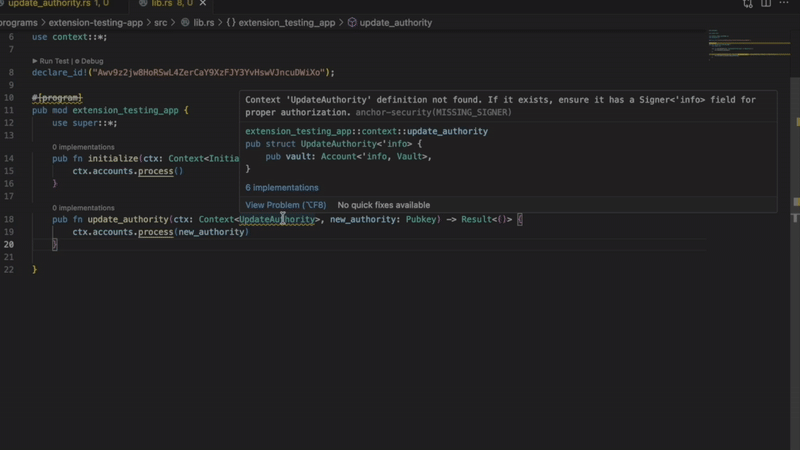
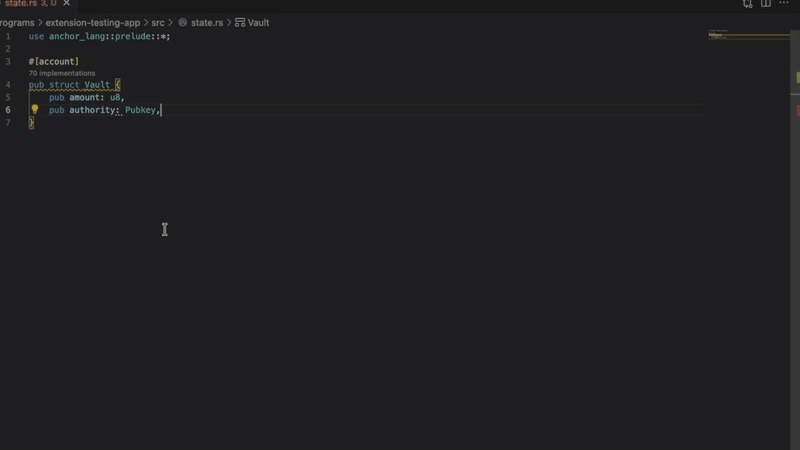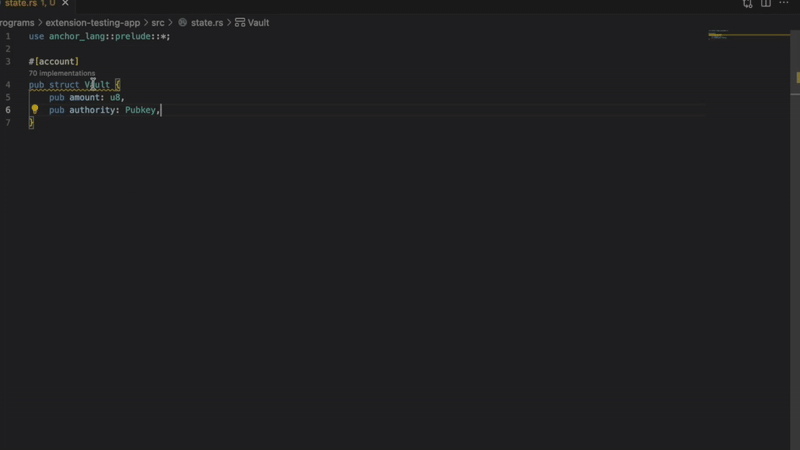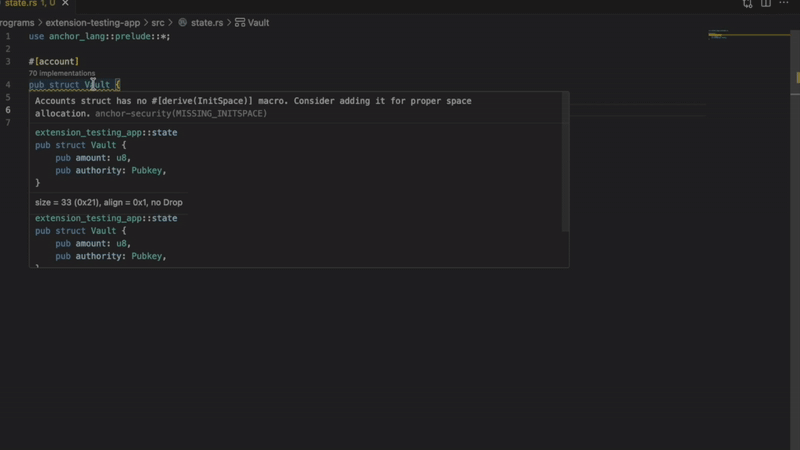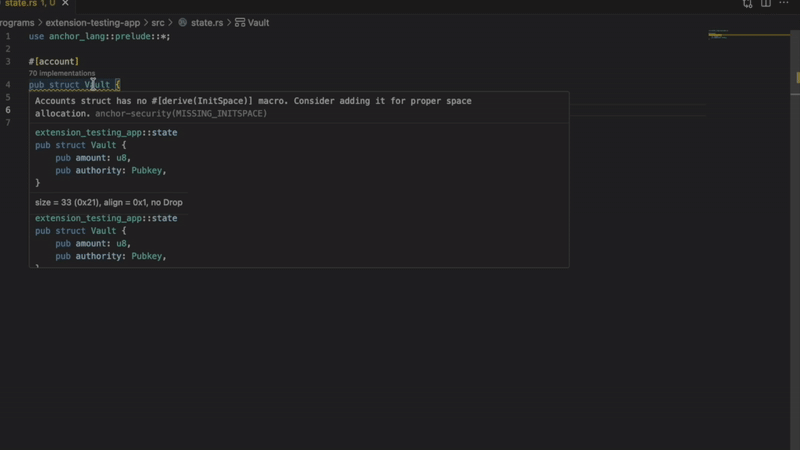
- Missing InitSpace
Detects account creation without proper space initialization. Prevents runtime failures when accounts don’t have enough allocated space. Critical for programs using Anchor’s init constraint.
- Unsafe math operations
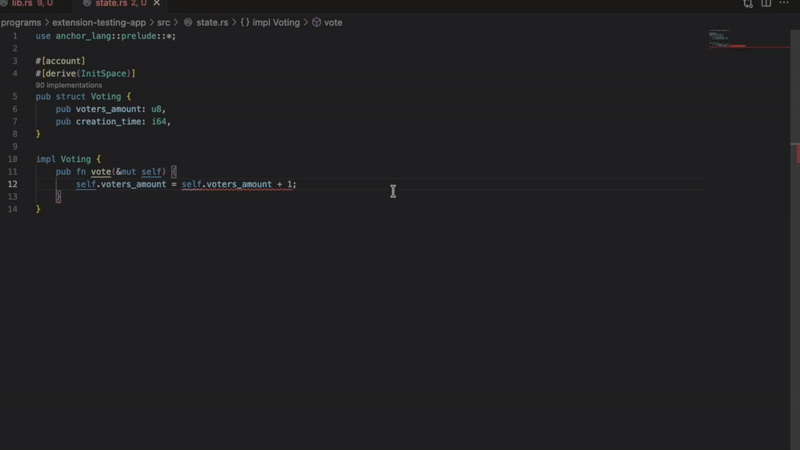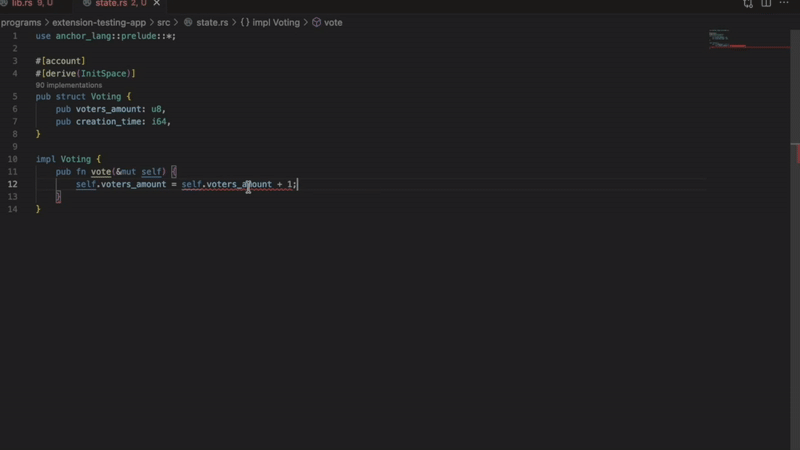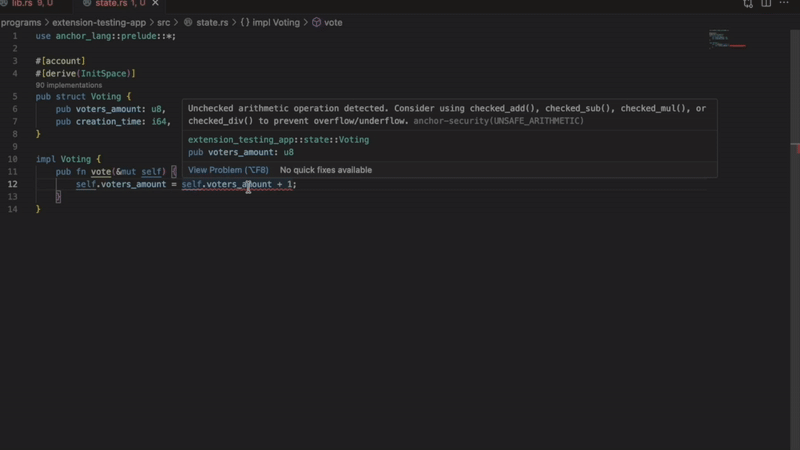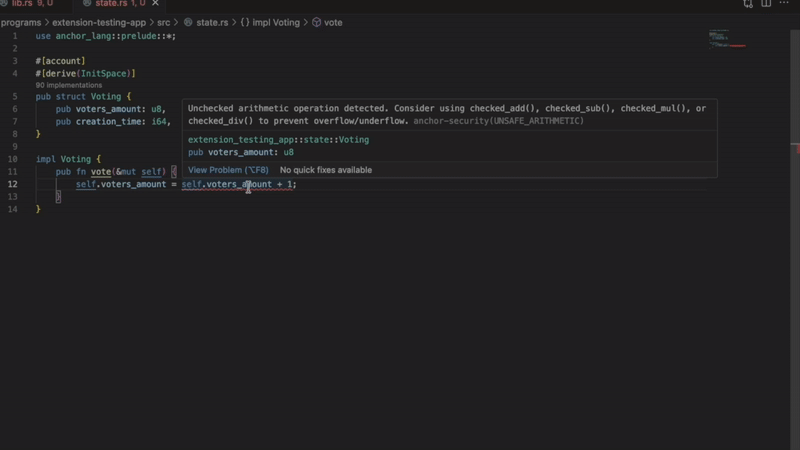
Flags arithmetic that could overflow or underflow:
let total = amount1 + amount2; // Flagged - no overflow protectionThe extension suggests using checked_add(), checked_sub() or checked_mul() instead.
- Manual lamports zeroing
Detects unsafe manual lamports manipulation. Manually zeroing lamports can bypass security checks and create vulnerabilities. The extension recommends using proper close patterns.
- Immutable account mutations
Catches attempts to modify accounts marked as immutable:
#[account]
pub config: Account<'info, Config>, // Immutable by default
// Later in code...
config.update(); // Flagged - attempting to mutate immutable account- Invalid instruction attributes
Detects incorrectly configured instruction attributes. Prevents runtime errors from malformed instruction definitions before compilation.
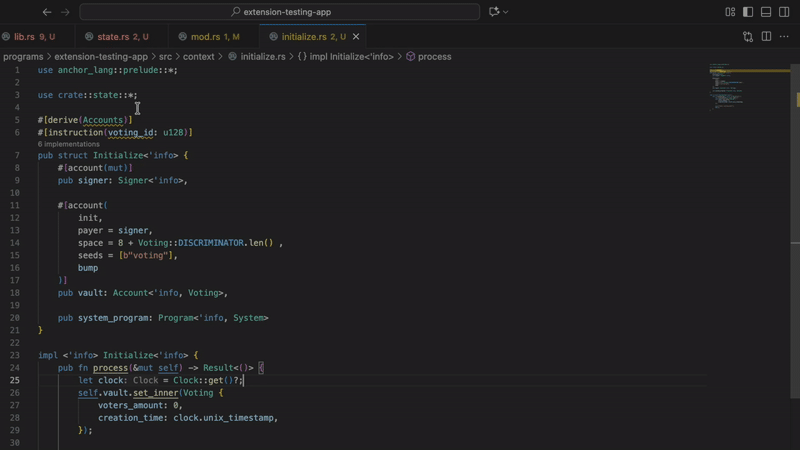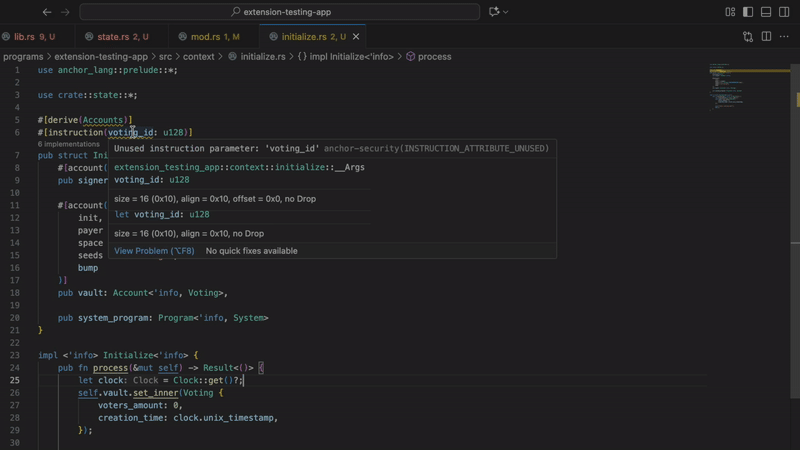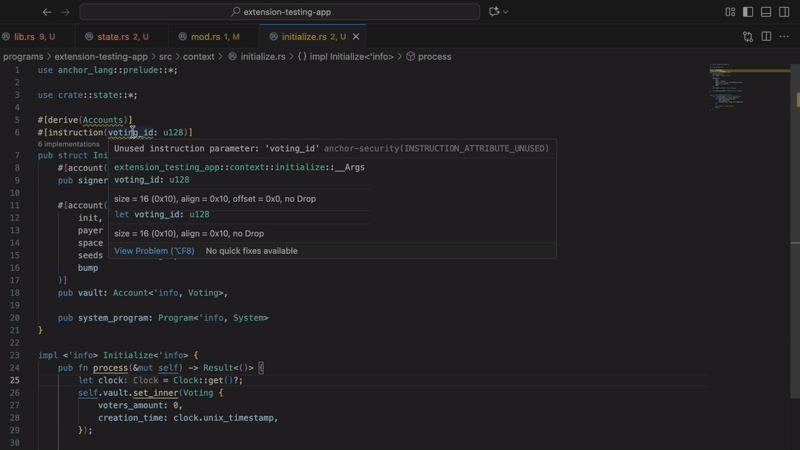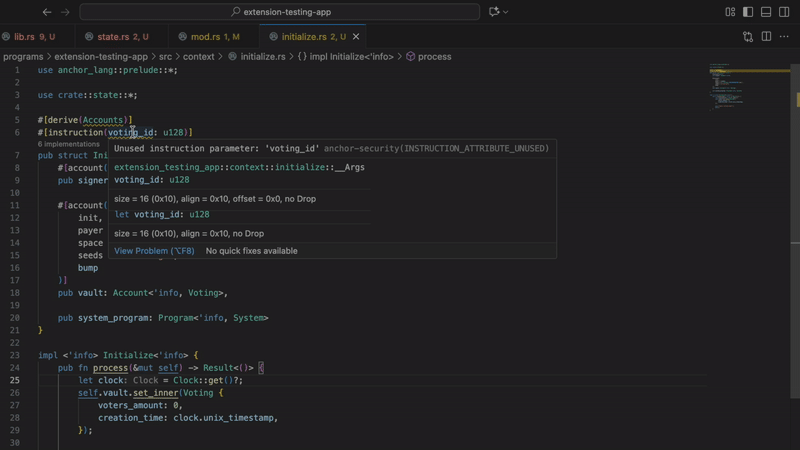
- Unused instruction attributes
Finds instruction attributes defined but never used. Often indicates incomplete implementation or copy-paste errors. Clean code means fewer bugs.
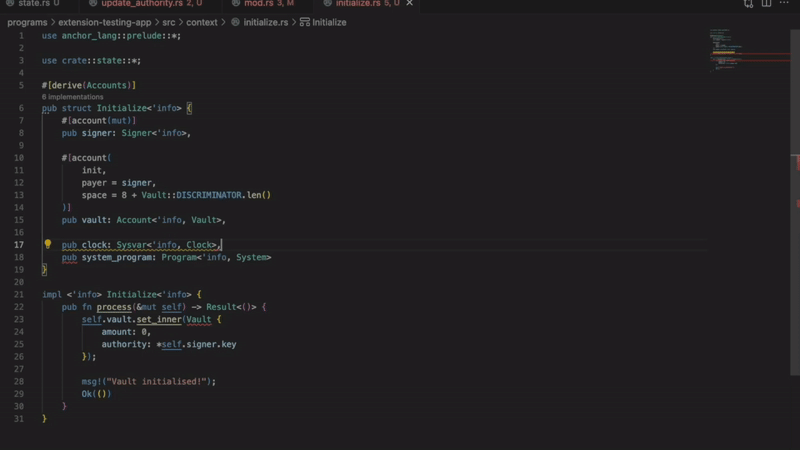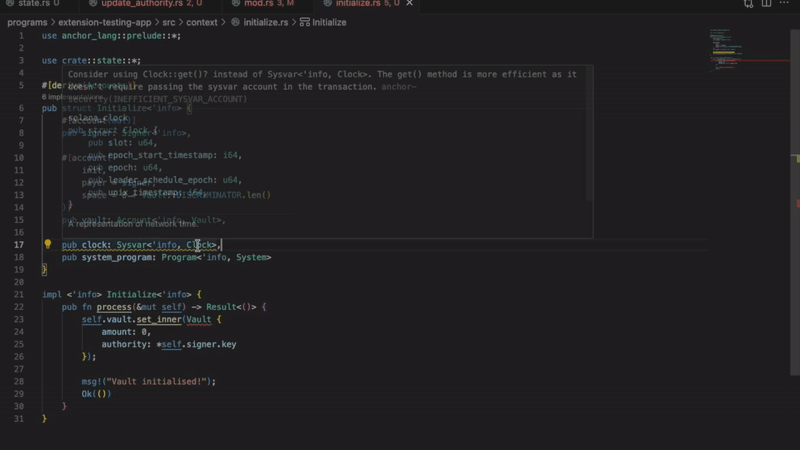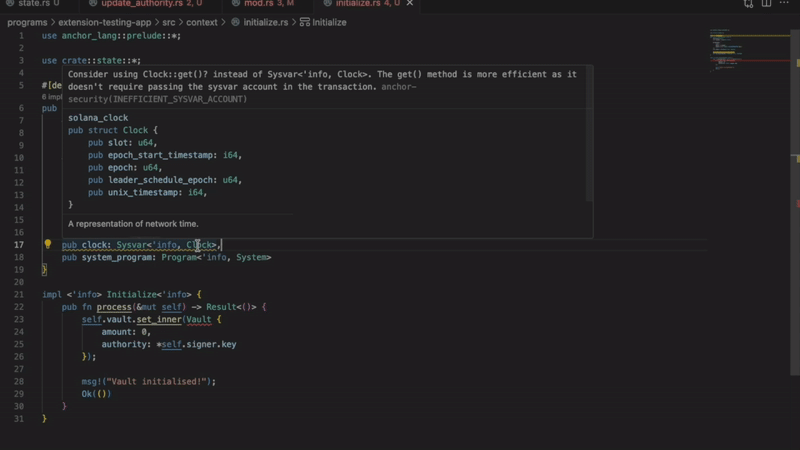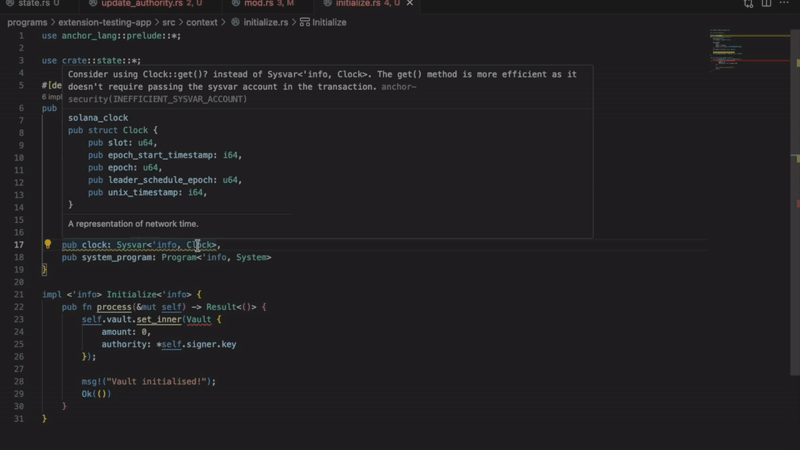
- Improper sysvar account access
Detects incorrect methods for accessing sysvar accounts. Using wrong access patterns causes transaction failures. The extension ensures you follow Solana best practices.
- Missing security check comments
Flags critical code sections without security documentation. Important for audits and code reviews. Documents why security-sensitive operations are safe.
How it works
The extension runs a Rust-based language server that parses your Solana programs and applies the nine detectors. Analysis happens on every keystroke.
When a detector finds an issue, you see:
- Red squiggle under the problematic code
- Diagnostic message explaining the issue
- Quick access via keyboard shortcut (Ctrl+Alt+S / Cmd+Alt+S)
All detectors are enabled by default. No setup required.
Fuzz coverage visualization
Unit tests verify specific scenarios. Fuzz tests generate thousands of random inputs to find edge cases. But without visibility, you don’t know what your fuzzer actually tests.
The Solana extension integrates with Trident to show exactly which code paths your fuzz tests cover.
Visual coverage in your editor
After running Trident tests with coverage enabled, open the coverage view in VS Code. Your program code displays with color-coded highlights:
- Green lines: Covered by your Trident tests
- Red lines: Untested code paths
- Execution counts: Number of times each line executed
This reveals gaps immediately. Error handling branches show zero coverage. Complex liquidation sequences remain untested. Overflow protection sits unexercised.
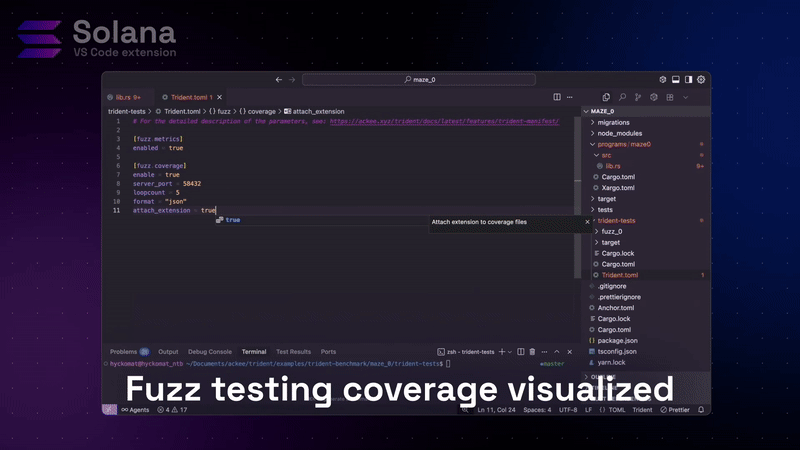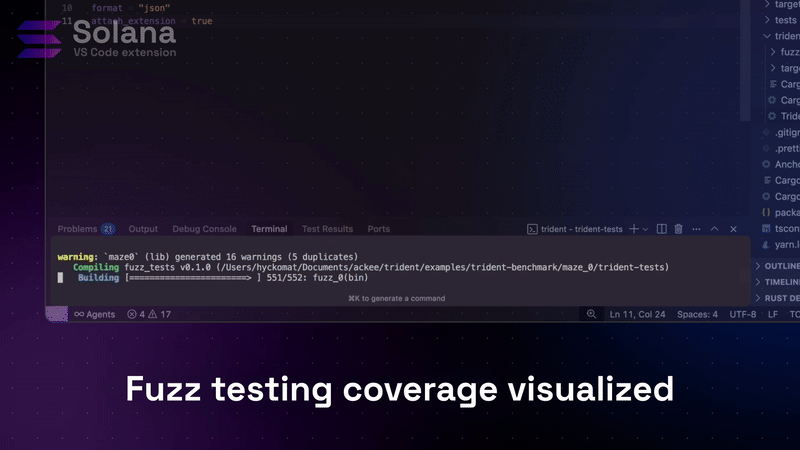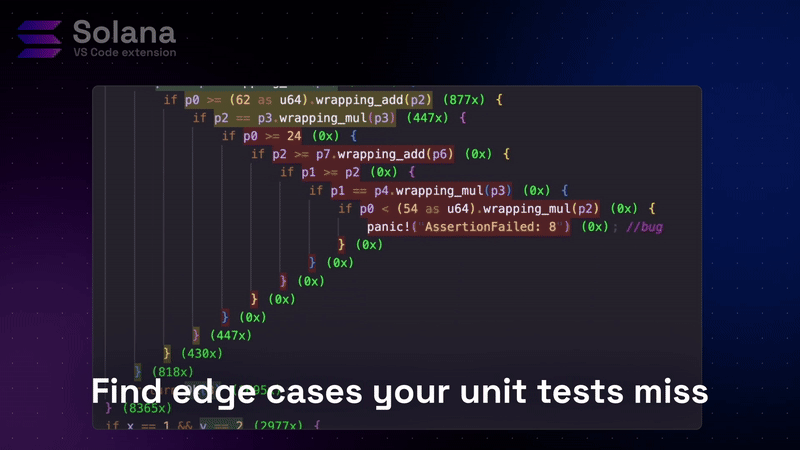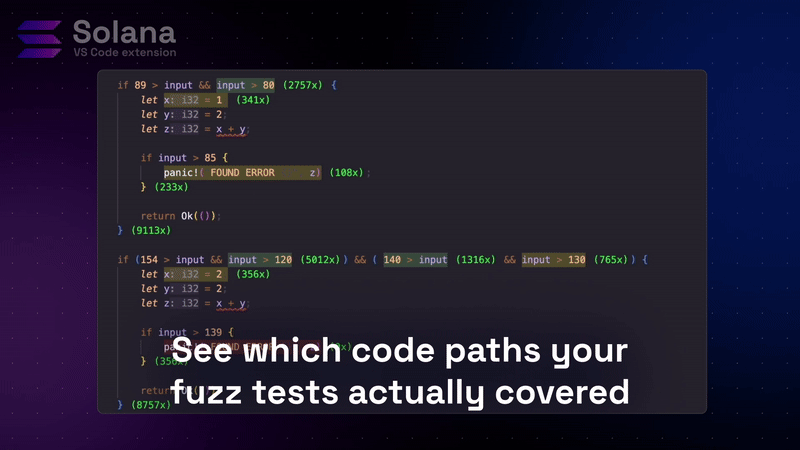
Real example
Consider a lending protocol with deposit, withdraw, and liquidation functions.
Initial coverage showed green across all deposit and withdraw operations. The team felt confident. Core functionality was thoroughly tested. But complex liquidation sequences showed red. The fuzzer wasn’t exercising the edge cases where liquidations interact with pending withdrawals.
They added targeted Trident flows for those scenarios. Re-ran coverage. The paths turned green. Then the fuzzer found it: a critical accounting bug in the liquidation logic that allowed double-spending under specific timing conditions.
Without coverage visualization, that bug would have shipped to mainnet.
How to use it
- Write your Trident fuzz tests
- Run tests with coverage collection enabled
- Open coverage in VS Code using the command palette
- Identify red (untested) paths
- Add flows targeting those paths
- Re-run and verify coverage improved
- Repeat until critical paths are covered
The visualization updates in real-time as you modify tests. No separate tool or context switching required.
Why you need this
Solana development operates at the intersection of high speed and high stakes. Even experienced developers miss things. Code reviews miss things. Unit tests miss edge cases.
This extension doesn’t replace audits or comprehensive testing. It adds two more security checks before production:
Static analysis catches common bugs as you type. Get immediate feedback in your editor rather than waiting for CI/CD pipelines or discovering issues during an expensive audit.
Coverage visualization shows gaps in your fuzz tests. Understand what your tests actually exercise, identify what they miss, and test with intention rather than hope.
Think of it as defense-in-depth:
- Layer 1: Anchor framework constraints
- Layer 2: Static analysis (this extension)
- Layer 3: Fuzz coverage visualization (this extension)
- Layer 4: Integration tests
- Layer 5: Security audits
This extension adds Layers 2 and 3. All layers work together. No single layer is enough.
Built by auditors
The nine detectors come from real findings in production Solana audits. They catch issues we’ve seen cost protocols millions. The coverage visualization integrates with Trident, the fuzzing framework we built and use for security testing Solana programs.
We built these tools because we needed them. Now they’re available to every Solana developer.
How to install
The extension is available now on the VS Code Marketplace.
Option 1: VS Code Marketplace
- Open VS Code
- Go to Extensions (Ctrl+Shift+X / Cmd+Shift+X)
- Search for “Solana”
- Open the 1st result (developed by Ackee Blockchain Security)
- Click Install
Option 2: Command Line
code –install-extension ackee.solana
Requirements:
- Visual Studio Code 1.96.0 or newer
- Rust and Cargo (latest stable) for security scanning
- Trident tests in your workspace for coverage features
Quick-start commands
After installation, access features via command palette (Ctrl+Shift+P / Cmd+Shift+P):
- solana: Scan Workspace for Security Issues (Ctrl+Alt+S / Cmd+Alt+S)
- solana: Reload Security Detectors (Ctrl+Alt+R / Cmd+Alt+R)
- solana: Show Code Coverage
- solana: Close Code Coverage
- solana: Show Security Scan Output
Security scanning runs automatically as you type. Coverage requires running your Trident tests first.
Roadmap
[Coming soon: We’re actively developing additional features based on community feedback and our audit experience. Follow @AckeeBlockchain for updates on new detectors, enhanced coverage features, and integration improvements.]
Conclusion
Solana developers no longer have to choose between speed and security.
The Solana VS Code extension adds real-time security analysis and fuzz coverage visualization directly to your workflow. Catch vulnerabilities as you code. See gaps in your test coverage. Ship with confidence.
It’s free and open-source and integrates with your existing workflow.
Built by the team behind School of Solana and Trident. Professional security tools from auditors who secure production protocols.
Install now from the VS Code Marketplace and start catching vulnerabilities before they reach production.