On April 14, 2025, the KiloEx protocol suffered a significant security breach resulting in approximately $7.5 million in losses. The incident stemmed from an oracle manipulation attack, highlighting critical vulnerabilities in the protocol’s access control mechanisms. Let’s dive into what happened and what we can learn from it.
Root cause
The root of the exploit was an access control issue in the protocol’s MinimalForwardercontract. The contract, which was inherited from OpenZeppelin’s MinimalForwarderUpgradeable contained a vulnerability in its executefunction that failed to properly verify signatures against provided data.
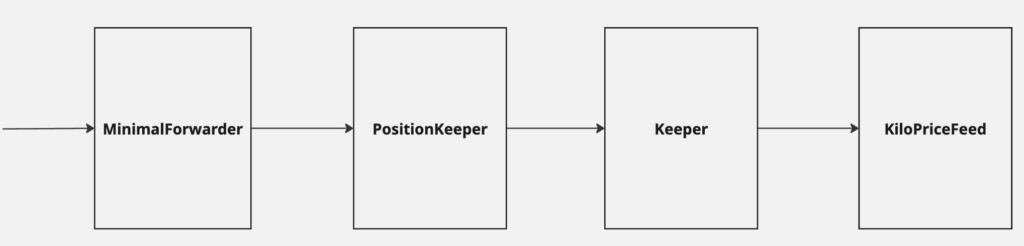
Trust model
The KiloEx protocol operated with a complex trust model involving multiple contracts:
- KiloPriceFeed → Keeper
- Keeper → PositionKeeper
- PositionKeeper → MinimalForwarder
- MinimalForwarder → Unrestricted Access
The critical flaw resided in the final link of this chain, where the MinimalForwarder contract essentially trusted any incoming request.
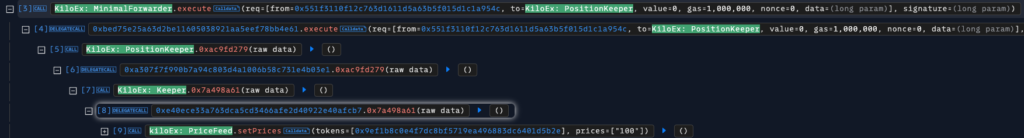
The attack vector
The attacker exploited the vulnerability by crafting malicious transactions that bypassed the intended access controls. To successfully execute the attack, they needed only to provide:
- A valid
fromaddress (obtainable from previous transactions) - A valid
signature(also observable from on-chain data) - Any arbitrary
toaddress (in this case, the PositionKeeper) - Custom
datafor function execution
What made this attack particularly concerning was that the implementation of the MinimalForwarder contract was not transparent and couldn’t be found on either BSC or Base.
Attack execution
The attacker executed their exploit through a series of calculated steps:
- Manipulated the oracle to decrease the asset price
- Opened long positions at the artificially lowered price
- Manipulated the oracle again to increase the price
- Closed positions for significant profit
Impact and implications
This incident is a reminder of several critical security principles:
- Access control is critical – Even inherited contracts need careful review and potential modification to ensure they meet specific security requirements.
- Trust model verification – Complex trust relationships between contracts require thorough validation at each step.
- Oracle security – Price feed mechanisms remain a critical attack vector in DeFi protocols.
Transaction evidence
The attack was executed across multiple chains:
Binance Smart Chain:
- 0x38b25be14b83fd549d5e0b29ba962db83d41f5f9072d0eac4f692fa8e7110bc0
- 0x1aaf5d1dc3cd07feb5530fbd6aa09d48b02cbd232f78a40c6ce8e12c55927d03
Base:
- 0x6b378c84aa57097fb5845f285476e33d6832b8090d36d02fe0e1aed909228edd
- 0xde7f5e78ea63cbdcd199f4b109db2a551b4462dec79e4dba37711f6c814b26e6
Key takeaways
- Always thoroughly review and test inherited contracts, especially their access control mechanisms.
- Contract implementations should be verified and accessible for security analysis.
- Relying on a single point of access control is risky; implement defense in depth.
Conclusion
For protocols looking to prevent similar incidents:
- Implement robust signature verification in forwarding contracts
- Maintain clear documentation of trust relationships between contracts
- Regular security audits with focus on access control mechanisms
- Consider implementing circuit breakers for significant price movements
This incident shows the importance of thorough security reviews and the potential consequences of overlooking access control mechanisms in smart contract development.